Google Workspace is used by 56% of American companies (2020). Not surprisingly, it is also one of the most secure solutions in the world. They are so into it that they recently released a whole series on Youtube: "Hacking Google".
Usage, the phantom threat
If you're using Google Workspace, you don't have to worry too much when it comes to the security of your data and infrastructure. One of the main things you do have to worry about is how your employees use Google Workspace.
How do they share documents with each other and outside your organization? How secure are their passwords? How do they share their calendars? How are group accesses configured? Did a departing user just use Takeout?
Banning? What for?
It's "easy" to protect yourself from data leaks, you just have to ban the behaviors that constitute it. This radical solution is effective on paper, but in reality it is more counterproductive than anything else.
Productivity as the first victim
This kind of solution is often synonymous with decreased productivity and friction for the teams. Sales and marketing teams are often in communication with the outside world and have to justify the profitability of their work time. It is therefore important for them to move quickly and avoid lengthy and unnecessary validation circuits.
They will always find a workaround to circumvent the prohibitions and maintain their productivity level. Bypassing means Shadow IT, and this is the best way to lose control of your environment.
Become your employees' ally
The key is to help your employees make optimal use of their software. You have to help them to use their software more securely without compromising their productivity. Yes, it is possible! All you have to do is to explain with pedagogy and to make your employees responsible by giving them the tools to protect themselves and your company at the same time.
This is made possible thanks to an existing tool in Google Workspace: the Admin console.
Use the Admin console to keep track of your users' behavior
As an administrator, the Google Admin Console is where you manage all your Google Workspace services.
The Admin console is your friend
You are using it to add or remove users, manage billing, configure mobile devices. But also to configure security rules for Google Workspace services. Creating alert rules in the Admin console is the most efficient way to control data breaches generated (voluntarily or not) by your employees.
How to set up the Admin console?
Setting up alerts on the Admin console is a fairly simple task. You need to go to your Admin console in the "Report Creation" section and then in the "Audit and Survey" section.
You can then select the service for which you want to access the logs (events). The console will show you all the activities performed by your users on that application. You are able to filter and drill down on each log to better understand what happened.
At the top of the page, you will find a section "Create a reporting rule". You can then set up your alert as you wish. Warning: some alerts are instantaneous, others may take several hours to land in your mailbox.
Behaviors to track on Google Workspace
Data sharing is the number one concern of security teams. So we suggest you start by following these 4 behaviors:
Sharing documents in public
Whether documents are shared internally or externally, file sharing is the best way to collaborate with other stakeholders. The problem is that file sharing can be very critical when it comes to the data they contain. When you share files outside of your organization, you want to make sure they don't fall into the hands of just anyone. We're talking about the infamous "anyone with the link" option.
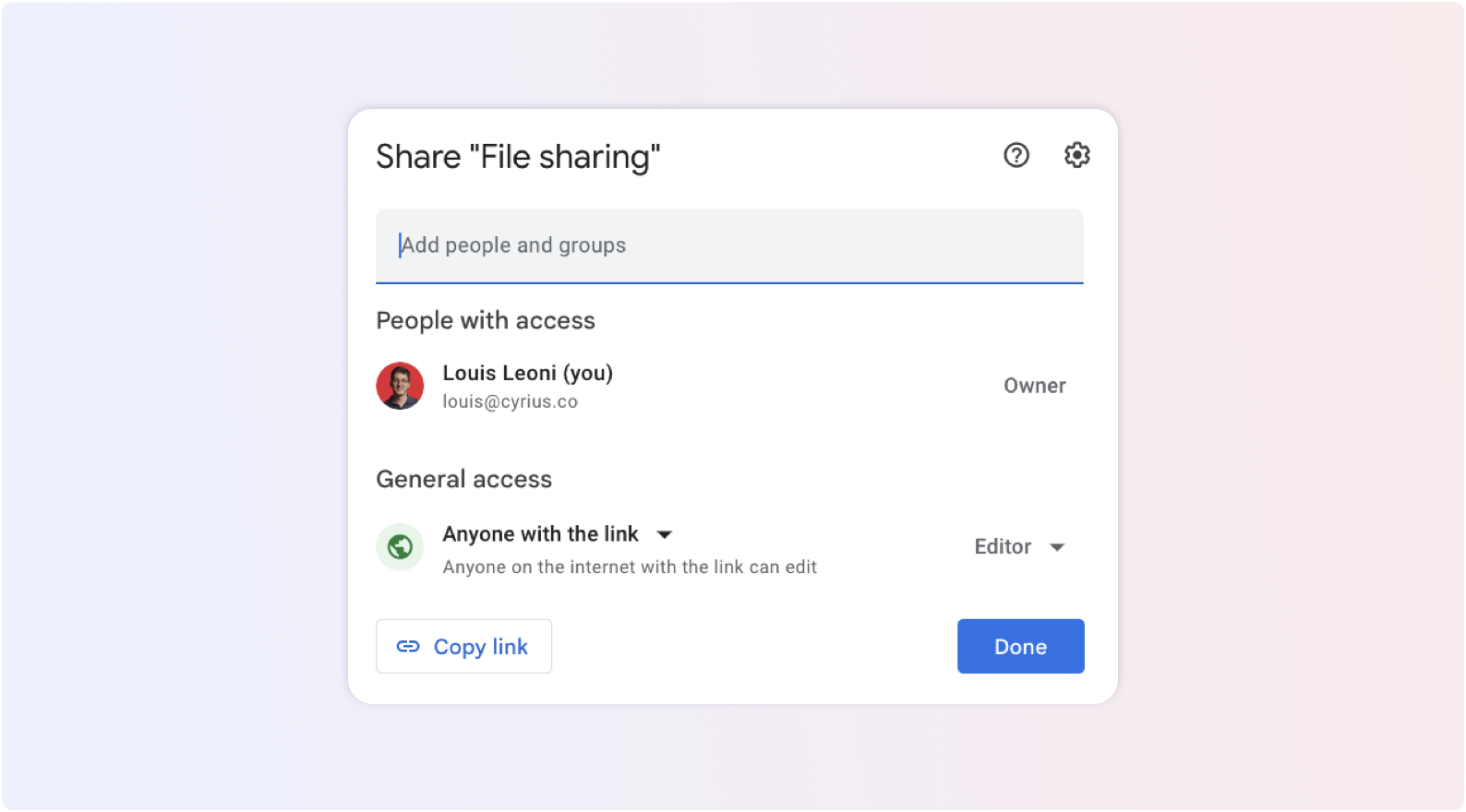
From the Admin console, you can set up an alert that warns you when an employee shares a document in public. Then, it's up to you to see with him or her to change the settings.
Public agenda sharing
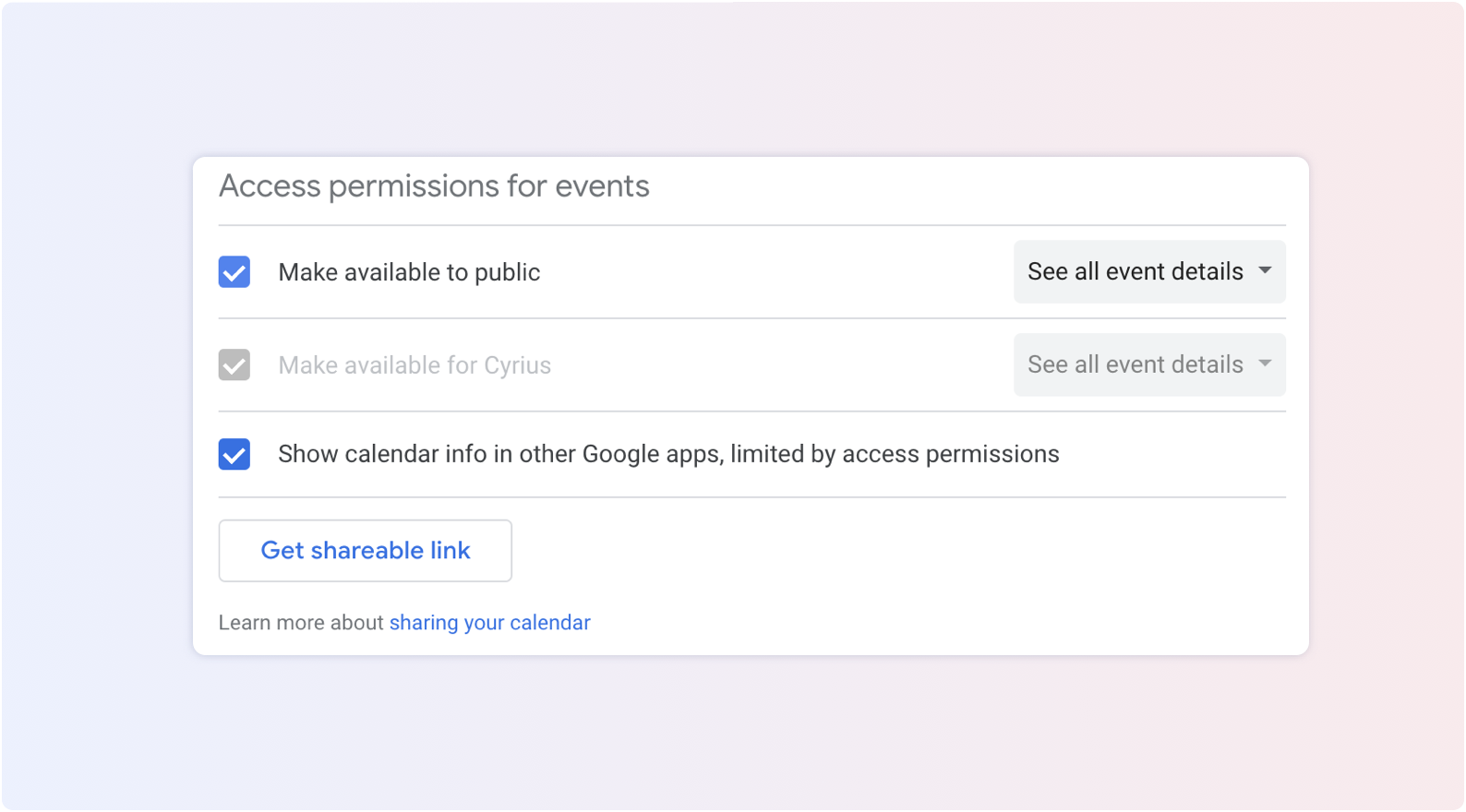
Agendas can contain confidential information. You want to make sure that no malicious actor can consult them: customer contacts, confidential meeting topics... Employees sometimes need to share their agendas with people outside your organization. To do so, they can share them publicly and this is an option that cannot be deactivated. So you have to make sure that doesn't happen.
Setting up Public Groups
Groups are a very effective way to quickly share information on a specific topic (marketing, technology, passion, etc.). You can create email suites to exchange with a large group of people within or outside your organization. Confidential information often passes through these conversations.
Public Group settings cannot be blocked by the Google administrator. They are chosen by the administrators of each Group:
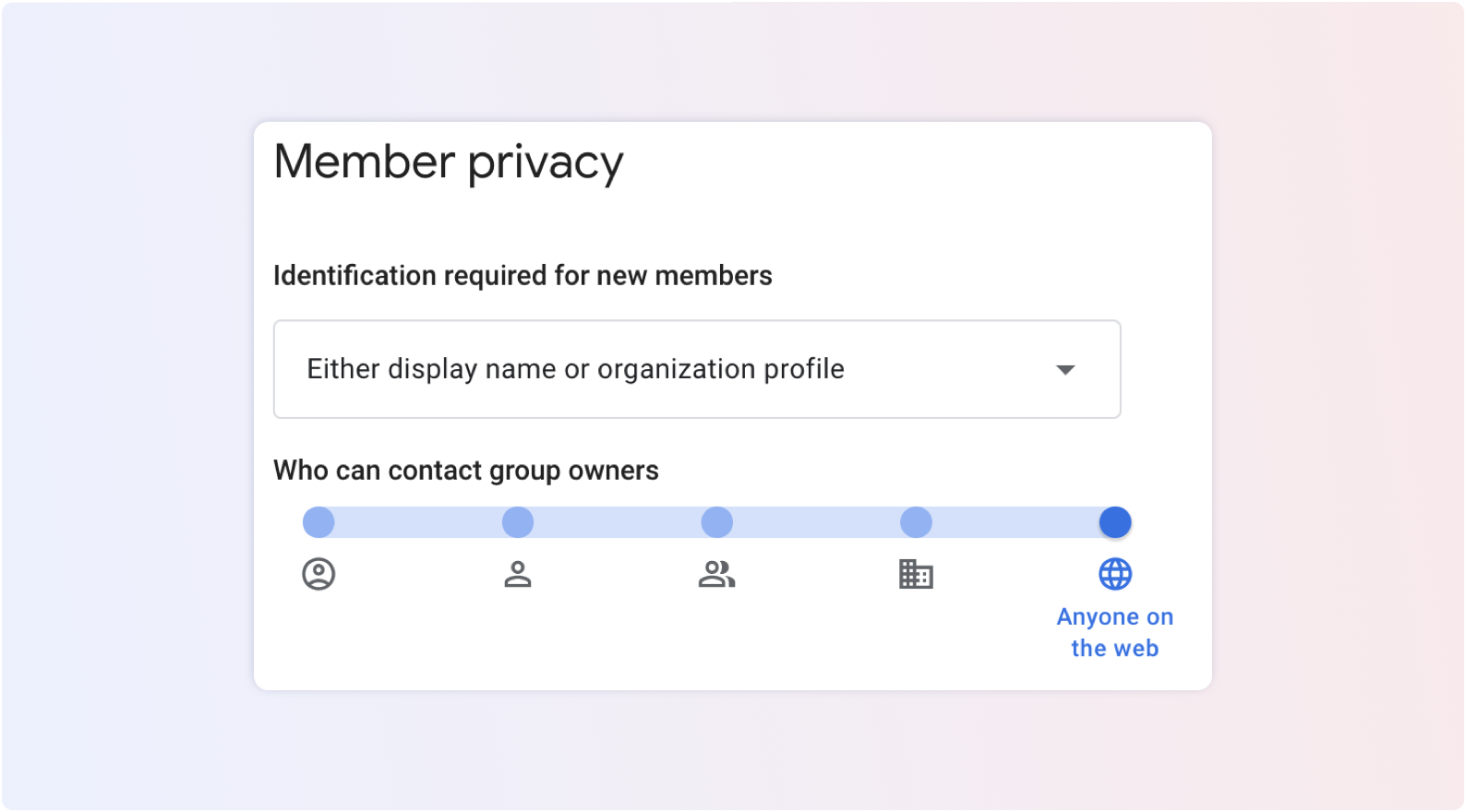
When a Group is public, a hacker can easily validate its existence. All he has to do is send an email to the group's address. If he doesn't receive a reply from Google telling him that the address doesn't exist, then it does. He is then able to usurp the email address associated with the group for phishing purposes for example. It is therefore essential to monitor the passage of groups in public on the three settings seen above.
Use of Takeout
If you don't know Google Takeout, you will like it. This Google service allows a user to export all the data about him: personal data, browsing history, documents, calendars, contacts... As an example, here are the data available for the Drive application. The goal of Takeout is to be able to transfer your data to another tool. However, you want to be aware when an employee uploads data from Takeout so you can take action if it is not legitimate.
Cyrius boosts your Admin console and protects your productivity
The Admin console is a very useful tool and can be quite sufficient if you don't have a large volume of event occurrences. On the other hand, notifications can be annoying and may not appear in real time. Managing these events can significantly increase your workload... .
Cyrius helps you configure the best security use cases on Google Workspace and go beyond the limitations of the Admin Console:
- Quick and intuitive use case configuration,
- Real-time notification of risky behavior,
- Resolve security vulnerabilities directly created by users,
- Visibility into resolved and unresolved vulnerabilities,
- Aggregation of the best use cases used by our customers
If this feels useful to you, feel free to reach out 👋